5 min read
If you think your organization is too small to be targeted by threat actors, think again. Over 60% of organizations have experienced an exploit or breach, so the stealthy and ever-evolving hacker may already be in your organization performing reconnaissance or awaiting strategic command and control (C&C) instructions. Businesses of all sizes are targeted by adversaries for a range of objectives, from monetizing data to making a political statement. Small and mid-sized businesses are especially at risk due to their limited IT and security resources and the evasive nature of advanced persistent threats. Organizations are now going on the offensive and considering a proactive approach to threat hunting given the evolving threat and risk landscape.
What is threat hunting?
Threat hunting can uncover threats you might otherwise not discover until some damage is done. Some organizations are already performing threat hunting, whether formally or informally, to detect data breaches sooner and reduce dwell time – the time cybersecurity hackers spend lurking in your systems and doing damage. Threat hunting is defined as:
The process of proactively and iteratively searching through networks to detect isolate advanced threats that evade existing security solutions.1
While not new, threat hunting has gained traction and focus recently as organizations look for additional ways to identify system and data compromise. Concerning threat management, a research study states that 43% of respondents ranked proactive threat hunting as an organizational priority for the next 12 months.2 More mature security organizations are taking a “hunt or be hunted” mentality to cybersecurity to augment alert management and incident response functions that tend to be more reactive.
Assess your threat hunting program.
Threat hunting can minimize or even counterbalance the risks of a data breach: lost revenue, decreased customer loyalty, defections among IT and security staff, and poor brand reputation. Some organizations with high security maturity and staff expertise may decide to build these threat hunting skills internally; whereas other organizations large and small may choose to augment their staff and skills with external threat hunting expertise. As Figure 1 below illustrates, organizations can evolve from a security foundations role to passive defense before adopting a more active defense capability. Network security monitoring is an essential and recommended step in the sliding scale. An active defense posture involves proactive learning from adversaries to use threat and log data to make smarter decisions faster.
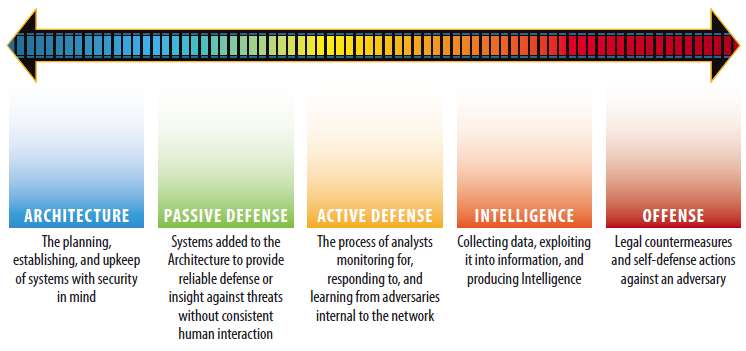
According to this SANS Institute framework, only the very largest and mature organizations and government entities have the resources to use legal measures and a true offensive position to combat cyber attackers.
Key benefits and considerations for threat hunting.
There are many advantages to a more proactive approach to cyber defense:
- Enhances the speed of response to threats
- Decreases investigation time
- Accelerates threat mitigation efforts
- Improves efficiency via a more formalized and consistent approach
- Increases visibility by better utilizing existing security tools like Security Information and Event Management (SIEM)
On the other hand, concerns about adding threat hunting to IT and security team workloads include the lack of data and visibility, a shortage of cybersecurity and threat hunting skills or staff, and the tradeoffs of proactive hunting versus day-to-day operational responsibilities such as alert and incident management. Larger firms may opt to have specific threat hunting analysts or to utilize external expertise for assistance. Embracing threat hunting can provide a cybersecurity payoff but requires planning and patience.
Tailor threat hunting strategy to your organization.
Proactive threat hunting can help identify adversaries faster and reduce the risk of data loss but requires balancing people, processes, and technology to be most effective. Businesses looking to embark on this journey should consider the following:
- Ensure your organization’s commitment to proactive threat hunting with executive awareness and even involvement. Threat hunting may involve a cultural shift for your company so educate organizational leaders on threat hunting and share that aggressive offensive techniques like “hacking back” are off the table.
- Develop a proactive approach that moves beyond more reactive incident response (IR). Start by creating an initial idea or hypothesis regarding where adversaries might strike and drill down in these systems, applications and logs for anomalies. Track your approach and progress to refine it and create repeatable processes over time.
- Understand how threat actors operate and the threat landscape for your organization and vertical industry sector. Think like a hacker and identify your most valuable and attractive assets to assess the tactics, techniques, and procedures (TTPs) that a threat actor may use.
- Leverage existing tools and resources such as SIEM monitoring to investigate indicators of compromise (IoCs). SIEM solutions such as our offer easy-to-use data filtering and fast searching that serves as a strong foundation for security analytics specific organization. Start small and stay focused initially as you hone your threat hunting skills and demonstrate progress to technical and executive leadership.
- Evaluate external assistance and expertise to elevate outcomes for your threat hunting that is typically done by more senior analysts. Not all organizations will have the commitment, focus, staff, and time to devote to threat hunting; external organizations and MSSPs (Managed Security Services Providers) can augment your team or even take on this role with your guidance. are a much more practical route for most IT security resource-strapped organizations.
You can watch the webinar “Let’s Go Threat Hunting: Gain Visibility and Insight Into Potential Threats and Risks” to learn more about where threat hunting fits in the threat lifecycle, what is needed to hunt, and how to start your proactive investigation process.
ENDNOTES
1 “Cyber threat hunting: How this vulnerability detection strategy gives analysts an edge – TechRepublic”. TechRepublic. Retrieved 2018-11-05.
2 “Threat Monitoring, Detection and Response Report: 2017”, Crowd Technology Partners. Retrieved 2018-11-07.
3 “The Sliding Scale of Cyber Security,” SANS Reading Room, August 2015, p. 2, Figure 1.


